Chapter 08
Privacy in Crypto- currencies
Since its inception, Bitcoin has been mistakenly portrayed in the media as anonymous. The opposite is, in fact, true. The transparent nature of blockchain technology ensures that every single transaction is recorded for everyone to see. In the case of Bitcoin, the metadata shows who sent what to whom and how much. Anyone who takes a look at the blockchain can see that privacy is very fragile and easy-to-compromise as it was based merely on pseudonymous addresses. These have become subject of thorough forensic analysis from both intelligence agencies as well as private companies such as Chainalysis.In the age of surveillance, the need for privacy has been ever increasing. It soon became clear that pseudonymity was not enough. The race for the best privacy protocol had begun.
At first, mixing services, also known as tumblers, appeared as relatively low hanging fruit. They were used to mix people’s funds with the intention to obfuscate the trail back to the original source. These were typically anonymous services to which one could simply send bitcoins along with instructions as to where they should end up afterwards, and soon they would get someone else’s coins. Tumblers usually charged between 1-3% of the transaction volume. This setup had a few significant drawbacks, though.First, it was based solely on trust, as the tumbler was an old school middleman, albeit an anonymous one. It was often the case that bitcoins sent never came back to the user and were lost forever. The user didn’t trust the service only with their own bitcoins, but also to not keep any records that could link either of the addresses involved. The main problem was that even when the service was honest, there was no way for them to prove they didn't sell these records, or that they deleted them in a secure manner. This was further improved upon by more trust-less methods such as CoinJoin, which was first described by Bitcoin core developer Gregory Maxwell in 2013. Not only did it solve the problem related to storing records, but it did not assume trust in the mixing service either. It allowed multiple users to get together and craft a single transaction with multiple inputs and outputs. To harden the privacy guarantees, this was meant to be repeated multiple times.
The idea of tumblers had to do a lot with the concept of plausible deniability. The main thrust is the ability to deny responsibility and knowledge of illicit activities that may relate to transactions the users were now linked to, due to mixing. So when Alice used one of the mixing services and ended up receiving bitcoins from a transaction that originated from a drug deal made by Bob, she could simply deny any involvement in the aforementioned deal and rely on the lack of evidence that made her denial plausible. In practice though, it is quite likely that Alice, or anyone else, would not want to be connected to any illegal activity whatsoever, even with a tainted UTXO, as it may cause some unpleasant situations in which one receives somewhat unwanted attention.
As Ian Miers, an applied cryptographer involved in both Zerocoin and ZeroCash, elaborated in his 2018 Devcon4 talk on problems associated with “decoy” systems that work with plausible deniability, they are vulnerable to various types of attacks and are especially vulnerable in repeated interactions that may create patterns in a transaction graph. By decoy systems, Miers means cryptographic techniques used in Monero, Mimblewimble, Coinjoin and alike. He suggests ZeroCash and Zerocoin as the best privacy-preserving protocols for layer one, BOLT protocol (Blind Off-chain Lightweight Transactions) for layer two, and ZEXE (a recently proposed protocol for decentralized private computation) for smart contracts. While, advisably, his words should be taken with a grain of salt as he has been personally involved with development of all the above mentioned techniques, his expertise as well as the significant importance of the protocols is undeniable.
Bitcoin's on-chain privacy got another flavor in 2016 with a proposal made by a group of researchers from multiple universities including George Mason University and Boston University. It went by the name Tumblebit, and while being a trustless solution, it involved two on-chain transactions, and therefore incurred more fees. It was eventually implemented by Bitcoin developer Ádám Ficsór in the Breeze wallet in the summer of 2018. The same person then implemented an upgraded version of (Chaumian) CoinJoin embedded into a privacy framework named ZeroLink that allows different mixing schemes in his next project, known as Wasabi Wallet. An interesting idea called Stonewall was also implemented by another privacy-focused Bitcoin wallet: Samourai. Stonewall transactions included some unnecessary transaction inputs and outputs in order to make regular transactions look like CoinJoin transactions. All these innovations have been vital to the development of the Bitcoin protocol, yet their usage has been reportedly low.
In recent years, financial authorities as well as intelligence services have shown an increasing interest in bitcoin mixing services. This trend was demonstrated in May 2019 when the Dutch Financial Criminal Investigative Service announced that it had seized the website of the bitcoin mixer Bestmixer.io, in a joint crackdown with Europol and other authorities, calling it “the first law enforcement action of its kind against such a cryptocurrency mixer service.” The focus was no longer only on the crypto on and off ramps. According to the views of US FinCEN, the institution responsible for combating money laundering and terrorism financing, pure crypto-to-crypto services were considered to be money service businesses, and thus must follow all the relevant regulations. As it turned out, Bestmixer.io operated from the Netherlands and Luxembourg, despite claiming to be domiciled in the Caribbean nation of Curacao.
With the increasingly tougher financial regulations led by European AMLD5, and de-anonymization techniques growing more sophisticated, blockchain analysis has become more available and intense than ever. As financial surveillance advanced, so did privacy seeking cryptographic implementations providing users with higher levels of confidentiality. While some of the anonymous coins such as Monero or Zcash have gained lots of traction in the past years, they were far from the first cryptocurrencies in this peculiar field.Probably one of the first, if not the first of such coins was AppeCoin (Anonymous Peer-to-Peer electronic Coin). AppeCoin’s design principles were drafted by Sergio D. Lerner in July 2012. The key premises involved untraceable tokens, unlinkable user accounts, private transaction amounts, and private account balances. As Lerner stated in the very same blog, at the time he was busy with other projects and did not dedicate much of his time to further development of AppeCoin. Two years later, in spring 2014, he wrote another blog where he published a draft of AppeCoin’s white paper, where he also lays out differences between AppeCoin and ZeroCoin, as well as ZeroCash protocols that had been proposed and started to get more traction:
AppeCoin is based on simple cryptography: the Decisional Diffie-Hellman in the polynomial samples setting, which was shown to be equivalent to the Decisional Diffie–Hellman (DDH) assumption, and also the Representation problem. So it should be easier to verify and trust the (finished) design and implementation of AppeCoin than of ZeroCoin or ZeroHash. Normally AppeCoin achieves full anonymization of a certain transaction gradually: each new confirmation block increases the output coins anonymity set size. Each miner shuffles the new coins with some coins of the block-chain, building a sequential Mixnet, and all the mixed coins are returned to the block-chain. When you pay with an unspent coin of the block-chain, the last shuffle operation it underwent is revealed. In contrast, in ZeroCoin/ZeroCash the anonymity set is maximal immediately: a new coin looks exactly equal to anyone in the block-chain when you try to pay with it. This is a trade-off AppeCoin does: it reduces the computational burden of transmitting a coin (and proving ownership of that coin) by increasing the cost of block verification. Nevertheless AppeCoin still allows you to get a user-selectable anonymity set by performing an anonymization operation yourself.
Lerner concludes his blog expressing sympathies towards ZeroCash, but at the same time he raises concerns about using zk-SNARKs (Succinct Non-interactive Arguments of Knowledge) as the security guarantee for a currency as it was fairly new technology that had not yet been battle-tested.
Zero-Knowledge Proofs
Before we explore zk-SNARKs, it is crucial to understand Zero-Knowledge Proofs (ZKPs). A zero-knowledge proof is a cryptographic method, first proposed in 1988, that lets person A prove to person B that she knows certain information, without actually having to reveal what the information is. Imagine you are going to a cinema to watch a movie that is only accessible to those above the age of 15. At the counter, you are asked if you can prove your age, and pull out your ID while hiding the date of birth with your fingers. And yet, you are allowed to enter the cinema, as the sole fact of you having the ID card proves you are above 15 (assuming you are in a country where IDs are issued at this age as in many European countries).
A legendary ZKP explainer called “How to Explain Zero-Knowledge Protocols to Your Children, or also known as the “Ali Baba Cave”, was published in 1998 by a team of researchers. Its simplified version goes something like this:Instead of Alice and Bob, we have Peter (the prover of the statement) and Victoria (the verifier of the statement). The two are in a cave whose entryway forks into two dark winding passages, one to the left and the other to the right. After a few meters, these two passages come together and form a circle-like shape of its ground plan. At the point where the passages are joined together, there is a magic door that requires a secret password to open it.

Source: thebitcoin.pub
Peter wants to impress Victoria and show that he knows the secret password. At the same time, he doesn’t want to reveal the password itself. Therefore, he tells her to wait at the entryway where the cave forks into the two passages. Peter takes either of the passages, let’s call them A and B. Victoria is not allowed to see, however, which passage he took. Peter reaches the magic door and notifies Victoria. She shouts back which passage he should use to return, either A or B. She chooses one randomly. Once Peter returns via the passage Victoria wished for, it is clear that Peter either knows the password, or was lucky to guess the passage Victoria will wish him to use. There is a 50% chance for both options. So they repeat the same process. After each successful repetition the chance that Peter was lucky significantly decreases. After they repeat it 20 times, the chance becomes extremely low (one in a million). At this point, Victoria has become impressed and recognised that Peter knows the secret password. And that’s approximately how ZKP works.ZKP is a technique deployed by an increasing number of not only cryptocurrency projects. Even though the concept was proposed over 30 years ago, the past few years marked a remarkable amount of activity in research and implementation. In 2013, an important paper was published proposing zk-SNARK (Zero-Knowledge Succinct Non-interactive ARgument of Knowledge). This iteration of ZKPs was implemented in Zcash later on.
In 2017, another group of scientists and researchers introduced Bulletproofs. A promising technique that got into Monero, Beam, Grin and is considered for Bitcoin too. Its great advantage over previous versions was that it did not require a trusted setup.Just a few months later, in 2018, another iteration causing a wave of excitement in the crypto world occurred, this time named zk-STARK (Zero-Knowledge Scalable Transparent ARgument of Knowledge), and considered for implementation in Ethereum. Moreover, this one promises to be resistant against the threats posed by Quantum computers. AZTEC (Anonymous Zero-Knowledge Transactions with Efficient Communication) protocol was introduced in the same year, in December 2018, and it allows for confidential transactions and assets on Ethereum. All of these iterations come with certain trade-offs such as proof size, verification time, (un)trusted setup, and more. It is likely, though, that we will see them being implemented in multiple cryptocurrencies in the years to come.
Zerocoin
Similar to Lerner in 2014, five years later, during our interview, Andreas Antonopoulos repeated similar concerns about the relation between “too much anonymity” and soundness of a currency. Both of these concerns build on the fact that the aforementioned technologies provide us with a such a high level of anonymity that it does not allows us to check integrity of the monetary supply of a currency as there is a hypothetical chance that under certain circumstances the monetary supply could be inflated by an attacker, and we may not know.This was a concern also with Zerocoin. It was proposed by professor Matthew D. Green and his students from John Hopkins University. While initially designed as an extension to Bitcoin protocol, it evolved into a separate network with an independent currency in the form of Zcoin. It utilized zero-knowledge proofs, and thus represented a vast improvement in protecting coins’ history and traceability. It had an inbuilt anonymizer where once could mint a coin by burning it up so it can be redeemed at a later time for a new (zero) coin. The new coin would have no transaction history and the link between the two would be broken. In the words of Zcoin creators:
…Minting a Zerocoin: You begin the minting processing by destroying a coin and generating a random serial number. You take this random serial number, and cryptographically commit to it so you cannot change it at a later time and post it on the blockchain. You can visualize a cryptographic commitment by thinking of it as putting a message in a locked box and putting this locked box up for everyone to see. This box is hung up on a giant notice board with everyone else’s lock boxes (the RSA accumulator). Only you have the key to open this locked box. So everyone knows that you have posted up a random serial number but don’t know what serial number it is (as they cannot open the box) and that you have burnt up a coin.Spending a Zerocoin: When you want to redeem your brand new coin, you do a Zerocoin spend transaction. You do this by putting on a disguise and showing proof that you have the key to open one of the locked boxes and also reveal the random serial number you cryptographically committed to previously. The proof is a zero-knowledge proof whereby people when seeing the proof can verify that you have the key to open one of the locked boxes, without revealing which box it was, merely that it is one of the many lock boxes that people have put up. Note that although you have revealed the serial number, other people still don’t know which lock box is yours since it remains locked. They still cannot see which lock box contained your serial number. This serial number is then marked as used so you cannot redeem another coin with the same cryptographic proof and the network grants you a brand new coin with no transaction history. …
The concerns related to auditability were, unfortunately, confirmed in April of 2019 when the Zcoin team discovered, and later announced, a vulnerability in the cryptography of the Zerocoin protocol itself. In this case, however, it was possible to detect the inflationary bug. As it turned out, it was a cryptographic flaw in one of the zero-knowledge proofs that had been present in the Zerocoin protocol since its inception. As the team disclosed, an attacker had exploited the vulnerability and was able to forge coins out of thin air. The amount created, however, should not have represented more than 1% of the overall supply. Naturally, this flaw affected all the cryptocurrencies that built upon Zerocoin protocol, such as PIVX and Veil, as they were vulnerable unless they disabled Zerocoin minting. This was not the first instance when an attacker inflated Zcoin’s money supply, as it happened already in early 2017. While the first instance was “fixable”, the second was fatal to the protocol. Nonetheless, until the vulnerability was found, the protocol was considered to be fairly advanced when it comes to providing financial confidentiality.
The original Zerocoin white paper depicts the process as you can see below. Note, the chain (a) shows how traceable transactions work in Bitcoin while the chain (b) shows how the privacy is improved by Zerocoin protocol.
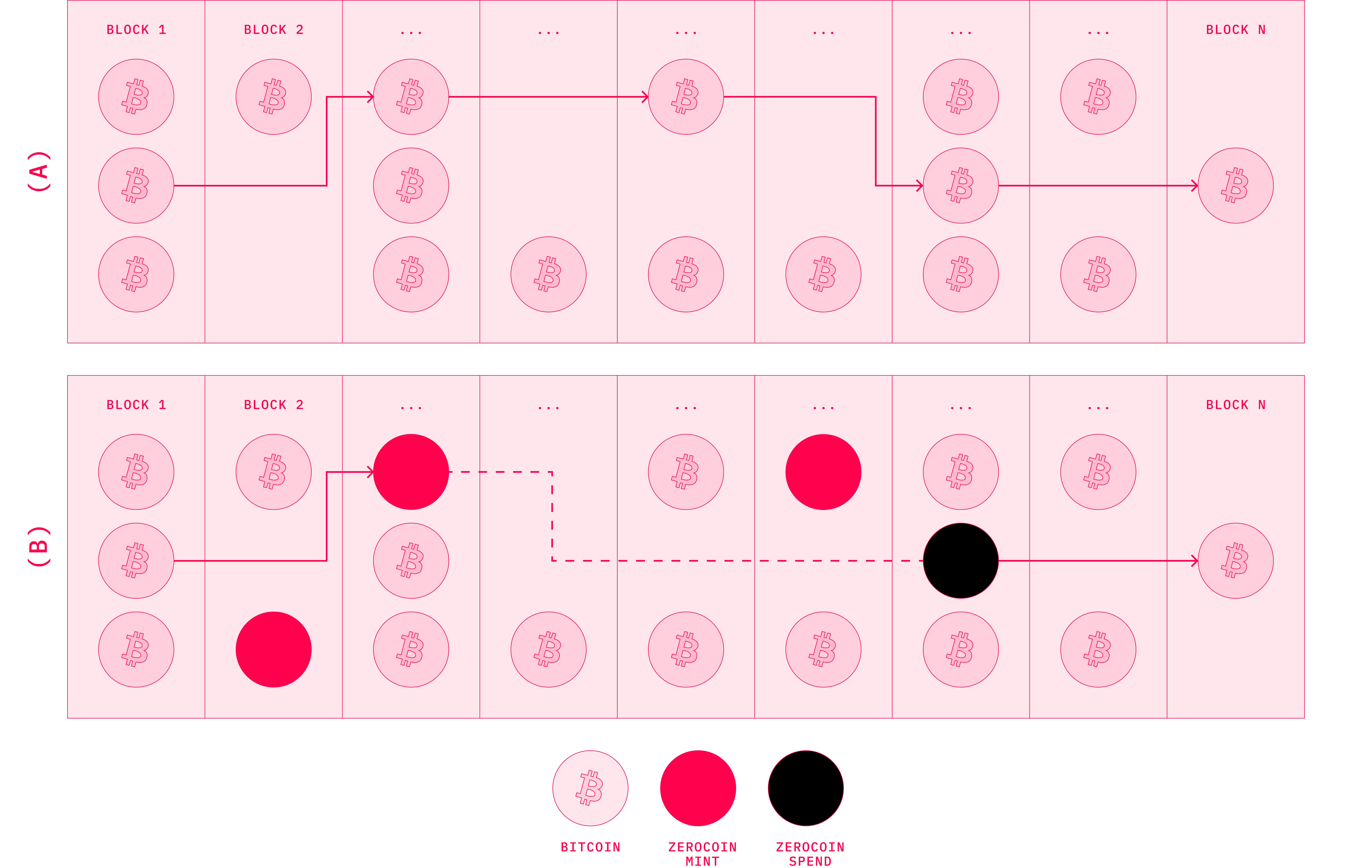
Source: Zerocoin White Paper
This scheme, however, had weaknesses. Since the newly minted anonymous zerocoins had the same denominations as the original coins (or bitcoins for that matter) the connection between the two could be detected, and thus anonymity compromised, if no other zerocoins, of the same denomination, were minted at the same time. Which was very likely to be the case in reality. Therefore, as a mitigation measure, it was suggested to only allow zerocoin minting in a set of predefined specific denominations like 1,5,10,50,100 etc. This feature was indeed implemented in both Zcoin and PIVX. It meant that the level of anonymity was derived from the number of mints in each particular denomination. Say we have a group of friends: Alice, Bob and Charlie. Alice mints and sends 5 zerocoins to her friend Dave. Bob and Charlie both owe money to their friend Eve, therefore they mint and send her 10 zerocoins each. In this situation, Bob and Charlie are more shielded relative to Alice since their anonymity set is based on the number of mints of their denomination, which is two. Meanwhile, Alice’s anonymity set based on the number denominations she used is just one.
As even the team behind Zcoin admitted, based on their observations, certain mint denominations are used less frequently than others, which naturally reduces anonymity of such transactions. Moreover, as payments in general are often recurring, these would be more vulnerable since there exist timing attacks that could guess which redemption of the previously minted (and spent) zerocoins corresponds with which burn. This represents a threat especially if there is a pattern between the burn and redemption process.This kind of setup, with fixed denominations, introduced another inconvenience which related to so-called “tainted change”. When you paid an amount smaller than was the UTXO currently being spent, you would naturally receive the change. If this change, however, was smaller than the smallest zerocoin denomination possible, typically 1, the change could not be minted and would be sent in a default form, and thus could compromise your privacy. Improvements to this were later suggested and implemented by the VEIL cryptocurrency. They turned zerocoin transactions on by default, and fixed the “change” issues by using RingCT, a cryptography technique which we elaborate on further in the chapter.
One of the protocol’s properties that was often subjected to critique from the community was the trusted setup. It was necessary to generate two very large prime numbers from which a parameter that cannot be easily factored was derived. This was done by a trusted party, and represented an attack vector and potential vulnerability. After the discovery of the faulty math underlying the protocol, most of the projects using it started their transition from the protocol. This includes Zcoin as well, which launched their new protocol — Sigma — on the main net in summer 2019, and works on their upcoming protocol Lelantus which builds upon Sigma and partially solves the problem with denominations. It brings also significant performance improvements, compared to the original Zerocoin protocol for example in reducing proof sizes from 25 kb to 1.5 kb and speeding up verification process from 300-400 ms per proof to 30 ms through batch verification, with the potential to reduce these numbers further via parallelization and pre-computation.
In the case of PIVX, it was not clear for long how the coin would move forward when it comes to privacy on their protocol. The team behind PIVX made some waves just a few months before Zerocoin’s critical vulnerability was discovered by implementing Bulletproofs into the protocol for the first time. This resulted in improving verification time and also significantly reducing transaction size. This was being worked on by Jonathan Bootle, one of the inventors of Bulletproofs. They were further improved by multiple cryptographers, including some of the Bitcoin Core developers such as Andrew Poelstra, Pieter Wuille, and Gregory Maxwell. To understand the main benefits of Bulletproofs, Stanford’s website sums it up:
Bulletproofs are short non-interactive zero-knowledge proofs that require no trusted setup. A bulletproof can be used to convince a verifier that an encrypted plaintext is well formed. For example, prove that an encrypted number is in a given range, without revealing anything else about the number. Compared to SNARKs, Bulletproofs require no trusted setup. However, verifying a bulletproof is more time consuming than verifying a SNARK proof. Bulletproofs are designed to enable efficient confidential transactions in Bitcoin and other cryptocurrencies. Bulletproofs have many other applications in cryptographic protocols, such as shortening proofs of solvency, short verifiable shuffles, confidential smart contracts, and as a general drop-in replacement for Sigma-protocols.
In early 2020, PIVX developers announced they once again were onto something with the planned integration of Sapling, a zk-SNARKs-based protocol created by the Zcash team. This should be the first iteration of Sapling in combination with PoS. The protocol named SHIELD went live in January 2021. Overall, the Zerocoin protocol represents a great improvement in the field of open blockchains when it comes to privacy and confidentiality, despite its weaknesses. While multiple teams tweaked the protocol in various ways to optimize for its inefficiencies, some of its original authors have kept contributing to the crypto space through other protocols.
ZeroCash
ZeroCash builds upon its predecessor while improving some of its features. Even though Zerocoin was allowed to break the links in a coin’s transaction history, the amount transacted was still out there for everyone to see. This is where ZeroCash leveled up the game as its cryptographic magic conceals the amount of money transacted. This largely mitigated the risk of aforementioned timing attacks. Though, it came with an important trade-off. This feature meant that under certain circumstances if an inflation bug occurs, such as in Bitcoin in 2010, an attacker could generate an arbitrary number of ZeroCash coins, inflating the money supply to whatever amount, say, a few hundreds of millions of dollars. Due to strong privacy, it is possible that no one could tell, and this whole event could go unnoticed, which is of course a problem.
This does, however, suggest an interesting point to consider when designing cryptocurrencies, as implied by both Lerner and Antonopoulos: the balance between privacy and money soundness. Bitcoin is seen by many as ultimate sound money with emphasis on predictable monetary policy, and thus supply. Increasing Bitcoin’s privacy at the cost of merely a hypothetical chance of compromising its supply’s integrity is likely to be considered unacceptable by the community. This is also a good reason to believe that there will always be space for altcoins. Their teams can afford to implement more progressive cutting-edge technologies and test them in the production environment, or using Bitcoin jargon, to be more reckless. Yet, the auditability risk exists on a scale. As Riccardo Spagni, the lead developer of Monero pointed out in our conversation:
That’s one of the things I have been arguing for lately; at the end of the day, Bitcoin is not immune to auditibility risks. And you can see that because there have been two clear inflation bugs on Bitcoin. The first was actually exploited in 2010 when someone created billions of bitcoins. Thankfully they didn’t spend it thereafter and there wasn’t a lot of traffic on the Bitcoin network at the time, relatively.The second one was a little more of an issue and that was the 2018 CVE, which was double spending transaction outputs. It was discovered and fixed before it could be exploited, but it existed for quite a while, for over a year. Thankfully, no one else discovered it and exploited it during that time.
This brings us to another interesting aspect to consider when we talk about privacy protocols, specifically about Zerocoin and Zerocash: parameter generation. In 1991, the American computer and network security company RSA Security, named after the initials of its co-founders Ron, Shamir, Adleman, after whom also the RSA algorithm itself was named, held a challenge to encourage research into computational number theory. They published so-called RSA numbers, a list of semiprimes, or numbers with exactly two prime factors, with a cash prize for anybody who could crack (factor) them. While the smallest number, made up of 100 decimal digits, was cracked soon after that, many of the numbers have not been factored until now and are considered to be safe for many years to come. The math behind it was rather “simple”. The company generated RSA numbers as “n” for which there always exists exactly two prime numbers “p” and “q” where the following is true:
n= p x q
The problem, and the challenge, is to find these two prime numbers if you are given only n. Some of these numbers, generated by the company in 1991, were used as initial parameters for the Zerocoin protocol. The reasoning here is that back then, it was not clear what all could be accomplished by cracking these numbers, and therefore there was little to no (monetary) incentives for the parties generating the numbers to cheat. The numbers were generated on a computer with no network connection, and the computer’s hard drive was subsequently destroyed to make sure there is no chance to recover the solutions. Almost 30 years after the challenge, most of the numbers indeed have not yet been cracked.
Inception of the ZeroCash protocol resulted in creation of cryptocurrency Zcash, and to conceive the network it was necessary to come up with initial parameters. The company behind Zcash, Electronic Coin Company, underwent its own “ritual” in order to generate these parameters. It is commonly referred to as “the ceremony,” and it involved six high profile personas from the cryptocurrency world. One of the Bitcoin Core developers, Peter Todd, took part in it, and wrote an extensive, and very interesting, blog post about the experience in November 2016. It was quite surprising, as later he took it down raising concerns that the ceremony might have not been a multi-party computation process after all, which would compromise the security of the network. A Multi-party computation process was there in order to ensure that the parties involved did not collude. In fact, it relied on an assumption that at least one person out of six will be honest, and delete their private key shard — also known as “toxic waste”.They made sure that all kinds of security measures were in place in order to mitigate any possible risks. The identities of the parties involved were not announced (even to each other) until shortly before the ceremony. During the ceremony itself, brand new air-gapped computers were bought from random stores just to get immediately inspected for potential hacks by security companies, and destroyed thereafter. All this was of course recorded, photographed, and recorded by multiple parties as well. Furthermore, the company as well as the whole ceremony was set up by some of the best cryptographers out there, including the company’s CEO Zooko Wilcox, a colleague of legends such as David Chaum and Nick Szabo. Still, the community has had their doubts as there is no mathematical proof that collusion did not happen. In the post summarizing the ceremony, Wilcox promised that in the future a counterfeiting-detection feature will be added, so anyone can measure the total monetary base of Zcash coins in circulation.Moreover, sending private transactions on Zcash required a higher use of memory, roughly 3.2 GB, and took significantly longer time, around 40 seconds (reduced to roughly 3 seconds in late 2018). This was according to Zcash’s benchmarks. Older machines could need as much as 30 minutes. On the other hand, Zcash required much less storage space compared to Zcoin. Again, Zcash represented a significant improvement in terms of privacy guarantees provided. Although, even in the words of Wilcox, it was highly experimental, risky, and unproven technology.
To understand the risks involved, we need to put into perspective the fact that the Zerocoin protocol used in Zcoin was considered to be the old and battle-tested technology using RSA cryptography that has been widely used since the 1970s. Yet, after many decades, fundamental flaws were discovered. Given this, along with the nature of cryptography, the question is not if, but rather when similar flaws will be discovered in Zcash.In spite of that, one cannot deny the potential of the underlying technology. But it wasn’t just anonymity where Zcash came up with innovations. As many other open source cryptocurrency projects, Zcash too was facing the riddle of sustainability of the protocol development when it comes to funding. The team decided to introduce the infamous “Founders reward”. The reward was offered in the form of 20% of the coin’s eventual supply. It was supposed to be released gradually as a portion of the block reward during the first four years, expiring in 2020. Despite the critique it has received from the community, it was an innovative approach to funding of an open source project as it basically allowed for traditional VC investors entering the cryptocurrency arena in a completely new fashion, while aligning with the long-term incentives of the developers, investors, and holders. The reward sparked lots of discussion in the crypto community in general, and later on even caused some forks of the protocol including Ycash, Zclassic, and ZenCash.
CryptoNote
Reportedly, just a few months before the Zerocoin protocol was proposed in spring 2013, a brand new privacy-centric protocol built upon a rather new codebase was announced by Nicolas van Saberhagen, who introduced CryptoNote. The first white paper was released in December 2012 while the second version was made public in October 2013. What is interesting is that the first cryptocurrency using this protocol — Bytecoin — was launched already in July 2012 even though it was only announced on Bitcointalk in 2013. The identity of Nicolas van Saberhagen remains unknown until now, similar to the case of Satoshi. Theories speculated that it may be someone from the Bitcoin community, mainly because the protocol has some ties to the Stanford Bitcoin Group. Moreover, like in the case of Bitcoin, we can find some interesting references directly in the Bytecoin’s blocks. Those from August 2012 contain, for example, quotes from Tim May’s Cyphernomicon, or Gibson’s Neuromancer. In our conversation, Andrey Sabelnikov, the person who coded the vast majority of the original Cryptonote's codebase, refuted Saberhagen's ties to Stanford Bitcoin Group:
The person behind this name is clearly one of the brightest minds I ever met. He is not related to the Stanford Bitcoin Group, and I don’t really know why he is not willing to be known, I believe one of the reasons is his very humble personality. Something like Satoshi in the privacy coins family.
As far as the protocol is concerned, it relied on cryptography primitives known as group signatures, first presented by Chaum and Heist many years before. The solution, however, was mainly built upon the work of Eiichiro Fujisaki and Koutari Suzuki called “Traceable ring signature,” while weakening its traceability property. Ring signature is a sophisticated scheme that does not allow a verifier to establish the exact identity of the signer other than that he is a member of the group of a few public keys. The other public keys' role is to be decoys. Likewise, your public keys may appear in a ring signature of dozens of other transactions even though you have nothing to do with them. This feature made blockchain analysis much more difficult.
The launch of Bytecoin was marked, however, by some suspicious circumstances. As some members of the community went on to investigate a bit the origins of the coin itself, they found out that even though the Bitcointalk announcement claimed the coin to be in existence, and more importantly, being used on the darknet, this did not seem to be the case. It became more interesting when Bitcointalk user “rethink-your-strategy” found out that the first version of Bytecoin’s white paper dated in December 2012 was most likely released a few months later. Even though the document itself was seemingly signed by the author in December 2012, as the aforementioned user discovered inspecting via Adobe Acrobat, the signing time originated from the signer’s computer, not a Timestamp Authority, as we would assume in this case. Moreover, the white paper’s footnote referenced a post from May 2013, and further analysis indicated that both versions of the papers were from 2014. By the time the coin was truly discovered by the community, roughly 80% of the supply was already pre-mined, and the reputation of the project was significantly damaged. Almost miraculously, Bytecoin has kept its market capitalization in the Top 100 for years. Anyway, its shady launch appeared to be a chance that many wanted to take advantage of. Bytecoin’s fork started to pop up at an accelerating pace. In a matter of few months the list included for example Fantomcoin, MonetaVerde, AEON, Paladincoin, Mountcoin , OneEvilCoin, NXTavos, DigitalNote, QuazarCoin , Dashcoin, Pebblecoin, Boolberry, Infinium-8, Buddhacoin, and Bitmonero.
Monero
Monero has been considered by many as the number one privacy coin. Its origin offers an interesting story on its own. It was launched as Bitmonero in April of 2014 by an unknown developer nicknamed “thankful_for_today”. Merely a few days after launch, the community decided to take it over and basically kicked him out. This was because of the series of disagreements he had with the majority of the coin’s fans. The “take-over” came, apart from the new team of developers, also with rebranding, and Monero was born. Monero's lead developer Riccardo Spagni a.k.a Flufyponny offers his view on why Monero survived and so many of Bytecoin's forks perished:
Basically, what it boils down to is all of those forks, except for maybe Boolbery, weren’t launched by the organization that created CryptoNote. I suspect where their mind went was Bitcoin has a bunch of forks like Litecoin and at the time Feathercoin, and VertCoin. These are all forks of Bitcoin that have value so if we can launch Bytecoin and then a whole bunch of really stupid forks, they’ll all have value and we’ll be able to fast mine them and dump them on unsuspecting idiots.What they didn’t expect, and it still fascinates me to this day that this is the way it played out, is that the very first fair launch, that first fork which was BitMonero, they did not expect that the community would take it over, that their sock puppet would be ousted by the community and the community would say “don’t worry, we’ve got this.To that end, Monero has only been successful because of that, because of being community-driven from that point when thankful_for_today was kicked out and told by [the community] that they’re running Monero and let’s see what happens.
Monero's privacy properties stem from multiple techniques, and the Ring signatures were not the only weapon in Monero’s arsenal of privacy tools. It further incorporated confidential transactions, or RingCT, which allowed one to hide the amount transacted, similar to Zcash. These were introduced in January 2017, and they were enforced by the protocol by default in September of the same year. Before that, Monero too relied on specific denominations, much like in Zerocoin’s protocol.
Stealth addresses were another important feature. They made sure the recipient's address was not recorded on the blockchain, as each Monero transaction was sent to a unique disposable one-time address. The recipient could access the funds sent to these addresses without revealing any links to their public address. To conceptualize the use of such addresses, imagine Alice wants to forward a message to Bob. She arranges have have Bob stop by her house to get it. Unfortunately, Alice needs to leave her house before Bob arrives, so she leaves the message in an envelope and asks her brother Charlie to give the message to Bob when he arrives. At the same time, she does not want Charlie to know Bob’s identity, so she tells him to give the message to whoever comes and says the code. In a similar manner, the Monero network uses one-time random codes to prevent the network from learning about the transaction recipients. This clearly improves the privacy properties as it basically allows for wallet addresses to stay off-chain.
But the Monero developers went even further, focusing on one of the most important features of a truly censorship resistant cryptocurrency — IP masking — which was done through Kovri. As in any P2P network, nodes communicate between each other by sending messages using IP addresses. The ability to link transactions to IP addresses has several downsides, as it allows for malicious nodes to geographically trace the origins of the data flow, and potentially block transactions from an IP address from being propagated through the network. The benefit of having network activity decoupled from the IP address was clear. Therefore, the Kovri protocol was designed to tunnel traffic through the I2P network while utilizing Garlic encryption and routing, an alternative to Onion routing used in the Tor network. It was planned to come bundled with future Monero releases to be enabled by default. In addition, Kovri features common APIs to allow other cryptocurrencies to use it as well.
Moreover, unlike many other cryptocurrencies using asymmetric encryption, Monero implements a more complex cryptographic framework which requires four different keys. There are two public keys: spend and view. And equally, two private keys. While a public view key is used to verify the validity of an address, a private view key is used to access data like the balance, fees, and transaction amounts. Note that it cannot create or sign transactions. Then, we have a public spend key used for transaction verification, and a private spend key used for signing and sending transactions. This also resulted in a difference in derivation of public addresses, as compared to Bitcoin where your address is generated via a hash of a single public key. Meanwhile in Monero, your public address is a direct representation of the pair of public keys. Existence of these key pairs allowed for view-only wallets, which was very handy for the purpose of audit, while maintaining confidentiality of outgoing transactions. This was due to the fact that ring signatures rely on spend state ambiguity, which means that revealing when an output was spent would result in identifying all the future (and past) appearances in ring signatures as a decoy. Therefore, not exposing outgoing transactions is important to maintain integrity of the network's privacy.
As of 2021, Monero is by many considered as the safe bet when it comes to the privacy coins, and it becomes increasingly more popular on Darknet marketplaces even though Bitcoin is still the currency of choice, as the report from Chainalysis suggests. Anyone interested in further details of Monero is recommended to read Mastering Monero. The book covers all the community and cryptographic principles that Monero embodies. More advanced tech-savvy readers are advised to read Zero to Monero.
Dash
Forked from Litecoin, Dash is one of the most famous cryptocurrencies on the market. It was launched in January 2014 under the name “Xcoin”. Soon after the launch, it was rebranded to “Darkcoin” which received rather negative publicity and connotations associated with the darknet, which resulted in another rebranding in 2015 to its current name. Dash was the first coin that introduced the concept of masternodes. Masternodes perform standard node functions such as relaying messages, storing a copy of the blockchain, and validating transactions. In addition to this, they have an extended role in providing governance and privacy. They vote on proposals related to protocol improvements, as well as route transactions that require extra speed or privacy, utilizing features called “InstaSend” and “PrivateSend,” respectively. Setting up a masternode requires depositing, or staking, 1000 coins into the user’s wallet that runs 24/7. Apart from masternodes, the ecosystem consists of regular nodes and miners.Dash was one of the first coins that users could use for increased privacy. That being said, the masternode network is an equivalent to other mixing services we know from Bitcoin. However, there was one significant drawback related to Dash’s stigmatic launch — “Instamine”. Instamine refers to an event at the very beginning of Dash’s history when in the first two days after the launch, over 2 million coins were mined due to a bug in the code. This represents roughly 11% of the overall monetary supply that will ever exist. The fact that the community decided to go on raises questions as far as the privacy of the protocol is concerned. It suggests that many of the network’s masternodes might be under control of a very few people, which has significant implications for privacy. Despite relentless defense from its developers, Dash has been subjected to an extensive critique within the Bitcoin community. This time perhaps, more accurately than other circumstances.
Mimblewimble
In the late evening of August 1st, 2016, an anonymous person signed onto #bitcoin-wizards IRC channel dedicated to “discussing theoretical ideas with regard to cryptocurrencies''. He dropped a link leading to a document hosted on a Tor hidden service, and signed out. The document is titled Mimblewimble and its author is “Tom Elvis Jedusor,” the French name for the Lord Voldemort from Rowling’s saga Harry Potter. Mimblewimble refers to the tongue-tying curse that binds the subject’s tongue to keep them from talking about specific topics.
At the time of this writing, there were nearly 150 million transactions committed in the blockchain, which must be replayed to produce a set of only 4 million unspent outputs.It would be better if an auditor needed only to check data on the outputs themselves, but this is impossible because they are valid if and only if the output is at the end of a chain of previous outputs, each signs the next. In other words, the whole blockchain must be validated to confirm the final state...
He goes on explaining the previous attempts to address this problem:
… Some solutions to this have been proposed. Greg Maxwell discovered to encrypt the amounts, so that the graph of the transaction is faceless but still allow validation that the sums are correct [1]. Dr Maxwell also produced CoinJoin, a system for Bitcoin users to combine interactively transactions, confusing the transaction graph. Nicolas van Saberhagen has developed a system to blind the transaction entries, and goes much further to cloud the transaction graph (as well as not needed the user interaction) [3]. Later, Shen Noether combined the two approaches to obtain "confidential transactions" of Maxwell AND the darkening of van Saberhagen [4].These solutions are very good and would make Bitcoin very safe to use. But the problem of too much data is made even worse. Confidential transactions require multi-kilobyte proofs on every output, and van Saberhagen signatures require every output to be stored for ever, since it is not possible to tell when they are truly spent.I call my creation Mimblewimble because it is used to prevent the blockchain from talking about all user's information [7]. …
The author further describes his innovative protocol that represents a new approach to tackle scalability and privacy issues on a public blockchain. In fact, it allows us to verify transactions without the need to store the entire history of the chain. In other words, it would need only 10% of the data storage requirements of the Bitcoin network. All of that while making it faster, more decentralized, and adding highly anonymous transactions. The protocol eliminates inputs and outputs of transactions as we know in Bitcoin, and replaces the UTXO model with one multi-signature for all inputs and outputs. There are no addresses. Instead, transacting parties share a “blinding factor” that encrypts all the inputs and outputs as well as public and private keys involved in a transaction. The blinding factor is a combination of public and private keys and it ensures that parties can prove ownership of the keys and that no new coins are created. This, however, results in a situation where both parties need to be online to transact. Nonetheless, the paper caused a much excitement within the community.A few months after the white paper release, in late 2016, another character from Harry Potter appeared on the scene. Someone using the name “Ignotus Peverell”, the original owner of the invisibility cloak, started on Github a project called Grin, implementing Mimblewimble in practice. The project received a lot of traction even beyond the Bitcoin community. Originally, the plan was to integrate it into Bitcoin protocol itself as a sidechain. One of the Bitcoin Core contributors Andrew Poelstra even wrote a more technical white paper elaborating on Mimblewimble’s properties. Ignotus was joined by a handful of anonymous developers and they decided to launch Grin as a completely new cryptocurrency that went live on January 15th, 2019.
Grin was not the first of Mimblewimble’s implementations, though. Beam, a competing implementation of the protocol, was launched just a few days earlier in the same month, even though Grin started with the codebase development over a year earlier, Beam caught up and managed to launch to the mainnet first. This was mainly because, while Grin remained true to the Cypherpunk principles and spirit, with open source governance, voluntary contributions of its developers, and community funding only, Beam launched as a VC-backed company utilizing a similar concept of the Founders’ reward like we know from Zcash.
But the funding mechanism of the two is not the only difference they have. They use slightly different mining algorithms, even though both are so far ASIC resistant. Grin is written in Rust language, while Beam is in C++. They also differ in their supposed purpose. Grin’s vision is to be more of a currency with infinite money supply, and initially rather high inflation, as one Grin is created each second. Beam tends to be in line with the “store of value” narrative as it has a finite supply of approximately 263 million coins. The funding has definitely an impact on differences in usability. Upon the mainnet launch, Grin was available only in a command-line wallet which represented a major obstacle for non-techies, especially when compared to Beam’s GUI. Overall, Grin represents a rather simple implementation laid out in the Mimblewimble paper. Beam, with more resources available, extends the protocol with further features, including opt-in auditability that might be appealing to the business world.
This difference, though, might translate into more tangible differences over time. As mentioned above, constructing a Mimblewimble transaction requires that both parties, sender and receiver, interact in order to create blinding factors. Grin’s tech stack uses a socket-based channel for a “real-time” session, meaning that the parties need to be online simultaneously. Beam has implemented a technology called Secure Bulletin Board System (SBBS) that allows for asynchronous communication. Furthermore, the team plans to implement one-sided transactions that would allow for something analogous to invoicing which might be much more practical for real-life payments. It will be interesting to see in the future how two different implementations of the same protocol, with different approaches to governance and funding mechanisms, will compete or complement each other.
Elixxir
Elixxir represents a re-appearance of David Chaum in the crypto scene, which caused a lot of excitement within the community since the project announcement by the “father of online anonymity,” who has been giving keynote speeches at many conferences across the globe. Elixxir describes itself as a “privacy-protecting decentralized transaction platform supporting messaging, payments, and decentralized applications that runs on a system called cMix, a minxes protocol for anonymous communications”. The protocol’s presentations have one key underlying topic present: the protection of metadata. Elixxir achieves metadata protection using two key components, minxnets and precomputation.According to the white paper, Elixxir’s mixnet represents an alternative to TOR’s onion routing:
Mixnodes perform the work of decrypting messages and mixing traffic to hide the associations between senders and recipients. The work of mixnets is performed in three phases: setup, precomputation, and real-time. In the setup phase, mixnodes establish secret and shared public keys, which can be used as a seed to derive unique values for every session. The precomputation phase is performed once for each real-time phase. The mixnodes establish shared values to circumvent the need for public key operations during the real-time phase, with each mixnode in an n-member team doing 1/n of the decryption work. In the real-time phase, mixnodes receive messages, perform the decryption work prepared for with precomputation, and pass the message on to the next mixnode.
The project, naturally, attracted quite some early investors, among them Chris Larsen, CEO of Ripple. At the time of writing, there is still not much information available about the project.
Other Cryptocurrencies focused on privacy
Privacy-centric protocol features have become increasingly more popular among various cryptocurrencies in the last years. Many forked their codebase from their older ancestors with minor adjustments, some made more hefty modifications, and a few of them built new protocols from scratch. As is the case in many instances, it is difficult to judge their long-term potential and relevancy in this field, but in order to depict the fullest picture possible, there are more coins that should be mentioned as they deploy at least some privacy-preserving techniques.
Secret Network, formerly Enigma, is one such protocol. Developed by researchers at MIT, it combines blockchain and off-chain storage to construct a personal data management platform focused on privacy, utilizing a network of “secret” nodes that perform computations over encrypted data. The protocol employs a verifiable secret sharing scheme to guarantee privacy of its computational model.
Particl, developed from a platform formerly known as ShadowCash, aims to become a global Amazon-like e-commerce platform with the expectation that all payments, transaction data, as well as conversations are routed through a decentralised network of nodes. The platform is equipped with a P2P encrypted messaging platform, stealth addresses, ring signatures, and end default use of Tor network.
Verge has been a rather controversial cryptocurrency that is often listed among the top anonymous coins, even though its protocol stack offers rather weak protection. It started in 2014 as Dogecoin Dark and rebranded in 2016. It allows sending transactions over the Tor network, and implements the “Wraith” protocol that allows for stealth addresses but offers no privacy for a sender. Moreover, the network was successfully attacked many times in the past, and thus is not a platform of choice for many privacy enthusiasts.MaidSafe is not typically found on privacy coin lists even though it is designed to offer a higher degree of privacy than most of the privacy coins. First envisioned in 2006, Safe network aims to redesign the Internet to its initial vision of a truly decentralized autonomous network with embedded privacy and security. The launch date is unknown.
It is important to add that privacy tools have been increasingly more common directly on-chain. While some of them are discussed in the next chapters, others have been released fairly recently and there is not enough information available to evaluate them adequately. There are mixed expectations about what kind of reaction the outburst of privacy coins will bring in terms of legislation as we move forward. While some expect retaliation and prosecution from the governments, perhaps surprisingly, a crypto pioneer such as Chaum did not seem to be so concerned about the issue when asked if he thinks that government will be upset about many of the blockchain projects becoming privacy-oriented, at the Lisbon’s 2018 Web Summit:
No, I think that privacy in the consumer payment space already exists. It's necessary. It's going to be very hard to extract that from Western democracies populations and it's not really a fundamental issue for criminal operations or terrorism or something. I mean moving large amounts of money around that's a different matter and it's kind of, you know, most of the US $100 bills are offshore and we don't know where they are and they're probably up to no good. And you know, you can move a little envelope of uncut diamonds around pretty easily. You don't see them on an X-ray machine when you walk through the airport.I mean, you know, the consumer payments is a whole different matter. You have to have privacy and I don't think that's going to be in fact of an issue when this stuff scales. You have to have it in order for it to scale, and it’ll never be picked up by consumers if it doesn't have it, and once it's deployed at consumer scale with privacy, it's a done deal. You'll never take it back.
At around the same time, I was in the audience to hear Chaum’s former colleague, the CEO of Zcash, Zooko Wilcox, at another conference called Devcon 4 in Prague, presenting his recent experiences from extensive meetings and consultations with US authorities:
You have probably heard that law enforcement and regulators and governments fear privacy, or that privacy technology like Zcash is incompatible with regulation, and I’m here to say that’s totally wrong. It’s not incompatible with regulation, and the actual regulators are not afraid of it and are not trying to prevent it.
He further backed up his claim by referring to the evidence that Zcash was approved by the New York Department of Financial Services to be traded at the Winklevoss exchange Gemini, prior that year. This alone should give legitimacy to privacy coins, from the legal perspective. While this might be true in some countries, the government's ban on crypto in India and China suggests that the opposite approach is equally possible, if not even more frequent. In 2021, the fact is that the status of cryptocurrencies, more so those with privacy preserving focus and features, is ambiguous, at best.
Conclusion
Nonetheless, as the global leaders talk increasingly more about a cashless society, the appeal of anonymous cryptocurrencies will just grow as they become more relevant. Elimination of cash has been on the radar for the same reasons the early digital currencies did not survive — governments’ ever-present eagerness to eradicate money laundering and trade of illicit goods. These efforts will eventually lead into a future where two parallel financial universes, the cashless and the bankless, will have to learn to co-exist together. It is likely that in many countries, anonymous cryptocurrencies will eventually be the only way to preserve financial privacy and freedom to transact. The privacy which one can achieve will move on a scale. While Bitcoin alone will likely offer options to obfuscate some of the transaction data, users with the desire to get the highest privacy guarantees possible will use other blockchains such as Monero, Zcash, Firo, or Pivx, or even more likely a combination of them. Built-in mixers are increasingly more common across the range of various crypto assets, not only Bitcoin. Ethereum alone features multiple such solutions in the form of Hopper, Heiswap, and Tornado. Moreover, it is not only mixers, but also a full-fledged privacy regime thanks to solutions such as Aztec protocol. And increasingly more chains are going this direction, even those that are commonly not thought of as privacy chains, such as Decred or Tezos. Proliferation of privacy techniques across the multichain crypto world is crucial in order to maintain cryptocurrencies' main purpose and their raison d'être: censorship resistant digital payments.